RelBAC: Relation Based Access Control
Project description
What distinguishes RelBAC from other access control models is the way it models PERMISSION in addition to the basic components such as SUBJECT and OBJECT. The intuition is that a PERMISSION is an operation that users (SUBJECTs) can perform on certain resources (OBJECTs).
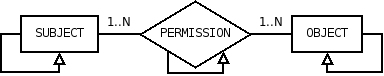
To capture this intuition a PERMISSION is named with the name of the operation it refers to, e.g., Write, and Read operation or some more high-level operation, e.g., Assign, Manage, etc. In RelBAC, the original form of a verb is used as a PERMISSION name with the first letter capitalized. The generalization (loops) on each components represent IS-A relations. They are the most common and important relations among the knowledge. Groups of SUBJECT and classes of OBJECT are organized with IS-A hierarchies. The most interesting part is the loop on PERMISSION which represents the IS-A relations among named pairs. Modeling a PERMISSION as a set of named pairs allows us to use set theories on PERMISSIONs.RelBAC allows to model and express access control policies and the related properties (e.g. separation of duty) in a simple way and to use the logic behind the model to reason about such properties.
People: Bruno Crispo, Fausto Giunchiglia
Publications:
- Fausto Giunchiglia, Rui Zhang, Bruno Crispo, "RelBAC: Relation Based Access Control",In the proceedings of the Fourth International Conference on Semantics, Knowledge and Grid. (SKG 2008) December 2008, pages 3-11.
- Rui Zhang, Alessandro Artale, Fausto Giunchiglia, Bruno Crispo, "Using Description Logics in Relation Based Access Control". In the proceedings of the 22nd International Workshop on Description Logics. (DL 2009), July 2009.
- Rui Zhang, Fausto Giunchiglia, Bruno Crispo, Lingyang Song, "Relation-Based Access Control: An Access Control Model for Context-aware Computing Environment", in Wireless Personal Communications Journal, Volume 55, Number 1, 5-17, DOI: 10.1007/s11277-009-9782-4. Springer 2009. (WPC).
- Fausto Giunchiglia, Rui Zhang, Bruno Crispo, "Ontology Driven Community Access Control". In the proceedings of the Trust and Privacy on the Social and Semantic Web Workshop. (SPOT 2009) June 2009. pdf
- Alessandro Artale, Bruno Crispo, Fausto Giunchiglia, Fatih Turkmen and Rui Zhang, "Reasoning about Relation Based Access Control", In the proceedings of the 4th IEEE International Conference on Network and System Security (NSS 2010), September, 2010
