xESB: Security Enhanced Enterprise Service Bus
Project description
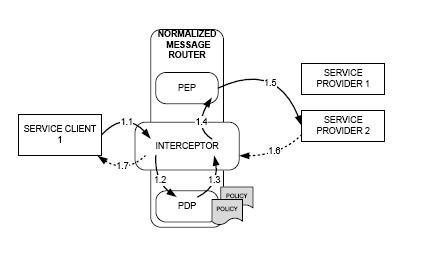
An Enterprise Service Bus is a state of the art piece of technology that deals with mediating communication throughout the enterprise. Enforcement of a policy comprises all the actions that need to be performed in order to makes sure that a policy or set of contraints is satisfied. xESB is an enhanced version of an ESB that monitors and enforces security policies both inside one business domain and between business domains. xESB is based on the Java Business Integration Standard which specifies a number of requirements for the SOA applications that are to be put together (or integrated). Because Java Business Integration is a standard, xESB is generic and applies to any JBI-based infrastructures.

- deletion or blocking of a message
- delaying of a message
- modifying of a message in terms of its metadata
People: Gabriela Gheorghe, Bruno Crispo
Publications:
- Gabriela Gheorghe, Daniel Schleicher, Ralph Mietzner, Ganna Monakova, Tobias Anstett, Bruno Crispo, Frank Leymann, "Combining Enforcement Strategies in Service Oriented Architectures". In the proceedings of the 8th International Conference on Service Oriented Computing (ICSOC 2010), December 2010.
- Gabriela Gheorghe, Paolo Mori, Bruno Crispo and Fabio Martinelli, "Enforcing UCON Policies on the Enterprise Service Bus". In the proceedings of the 12th International Symposium on Distributed Objects, Middleware and Applications (DOA2010) On theMove Federated Conferences, October 2010.
- Gabriela Gheorghe, Stephan Neuhaus, Bruno Crispo, "xESB: an Enterprise Service Bus for Access and Usage Control Policy Enforcement". In the proceedings of the Fourth International Conference on Trust Management (IFIPTM10), June 1 2010.
- Gabriela Gheorghe, Fabio Massacci, Stephan Neuhaus and Alexander Pretschner, "GoCoMM: A Governance and Compliance Maturity Model". In the proceedings of the 1st ACM Workshop on Information Security Governance, November 2009.
